Password managers: LastPass and ProtonPass
Over the last several months, I’ve been asked for advice on password managers. I am not a security researcher. I can only tell you what I do, and why. My experience and context are that I primarily use MacOS and iOS, as well as one Windows laptop. I was a LastPass user for a decade, but switched this year to ProtonPass.
- I’ve made my peace with cloud-storage for my passwords because I think the convenience outweighs the risk.
- Browser integration with a plugin is very convenient, for both retrieving and automatically updating or storing passwords.
- If you have a lot of Apple devices, then Apple will auto-fill the password for you in many, many places.
- On iOS, you can choose which password manager to use (e.g., LastPass or ProtonPass).
Evaluation
At one point, I put together a small evaluation matrix for a colleague, shown below.
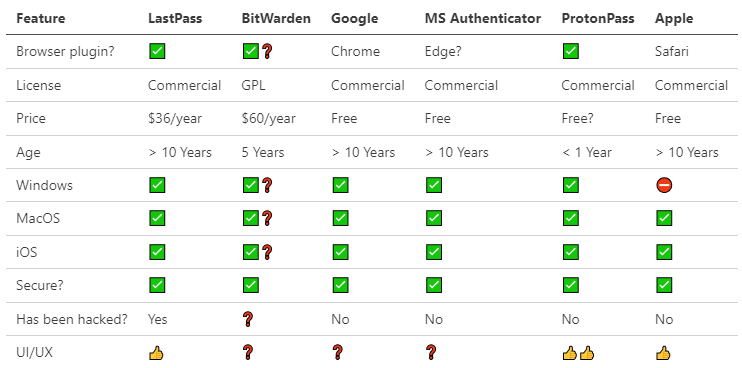
As you can see, I don’t know that much about BitWarden, nor am I familiar with the UI/UX of Google or MS Authenticator as integrated into their respective browsers. What I do know is that any browser-specific solution—this applies to Firefox as well—is quite limiting, in that you generally can’t use the password managers in other browsers or contexts. An ideal solution is to have passwords auto-filled in whatever context you find yourself in.
LastPass
LastPass works well, as you can see above. I used it for about a decade. Why did I stop?
- I already have ProtonMail and ProtonVPN, so I got in early with ProtonPass and was pleasantly surprised by how much cleaner and smoother the UI was than that of LastPass. I was able to easily export and then import all of my passwords.
- Shaky implementation of “ignore this site” that would constantly ask me to store a site every time I created a link in Azure DevOps.
- A few very public breaches that, while I’m sure didn’t reveal any of my passwords, still ensures that my data blob is out there for everyone to see. Fingers crossed 🤞 that their encryption implementation is solid.
What’s still better about LastPass?
- LastPass does auto-fill usernames and passwords more reliably.
- It also picks up password-changes more reliably.
- It allows you to paste credit-card information all at once.
Those advantages come with a caveat, though: sometimes it pastes too much information, or information into the wrong boxes. The whole “paste and go” has become increasingly shaky, as UIs change and no longer reliably present patterns that password managers expect.
ProtonPass
ProtonPass does everything that LastPass does, but with a few UI and feature improvements.
- ProtonPass allows you to set a timeout and pin code to re-encrypt your in-memory data. The pin code is easier to enter than your master password—and also easier to guess—but it makes it more secure. Your data in-memory isn’t encrypted with your master password (as it is at rest and in transit), but it is at least not in plain-text in memory.
- It also integrates an email obfuscator that actually seems to work with modern sites.[1] This lets me avoid giving my real email to any old site.
- The UX is more stable and friendly. I can copy/paste an item, then quickly return to the dialog and it’s still open to the same information. LastPass would always reset, so you’d have to search for a site, copy the username, … then search for the site again to copy the password.
Adding and updating credentials
As noted above, ProtonPass is less aggressive about picking up changed passwords or filling in existing ones. I imagine that this is because they try less hard to detect every possible pattern that a site might use. I kind of agree that it’s better to make a good, stable UI that lets you easily copy/paste information than to try to keep up with the myriad ways that web sites are making authentication inconvenient for password managers.
For example, when I updated a password recently, I noticed that LastPass would pop up and ask me to store the password … but it was kind of annoying because it would ask too often. But I noticed that ProtonPass doesn’t ask nearly as often—though always more, with each update.
Even if it doesn’t offer to let you generate password, you can generate one manually.
When you add a password with ProtonPass, it hangs onto it for a while in the “generated passwords” area:
ProtonPass recommends reversing your workflow. Instead of clicking in the popup to generate a password, you should go to the “change password” page, then click in the plugin and generate a new password from there. It’s pretty easy, and it can auto-fill it from there. Here’s a little video:
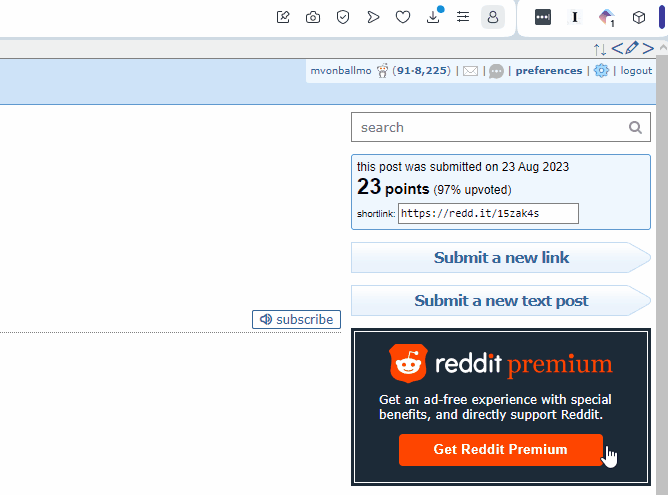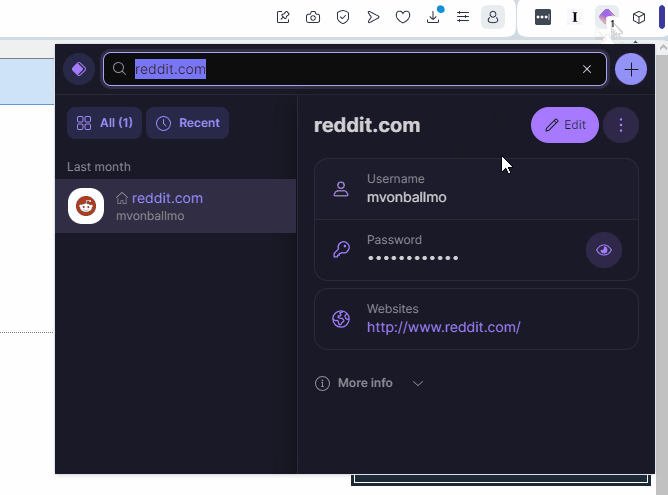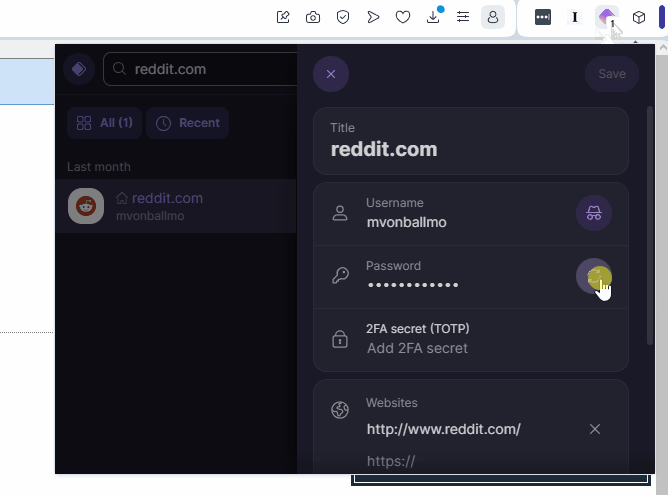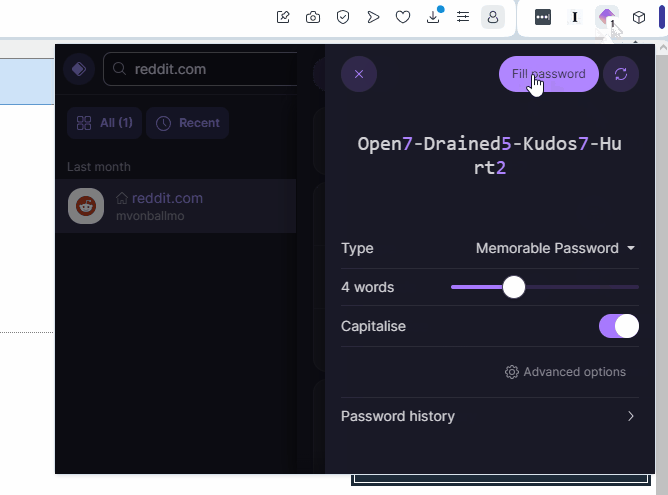 Generate Password with ProtonPass
Generate Password with ProtonPass
A layman’s thoughts about password-manager security
I’m going to repeat that, while I’m quite technically adept, I’m not a security expert. I read a lot about it. I haven’t caught wind of any problems with the implementation of either LastPass or ProtonPass. I wrote the following to a colleague about a month ago.
The primary thing for any of these providers is to keep the data encrypted at rest, in transit, and, as much as possible, in memory. Decrypting should only ever occur on a client device. That information should only remain decrypted long enough to use it—with an appropriate timeout.
Both their algorithms are solid and the number of cycles they require ensure that it would take more computing power than anyone has centuries to crack with brute-force. In this way, they’re the same as any other provider, like Apple, Google, 1-password, BitWarden, ProtonPass, Keepass, etc.
That’s the most important protection that any of these providers give you.
The algorithmic protection is, as noted above, only as good as your password. The algorithms together with a strong password, protect you from brute-force cracking. If you have a weak password, then attackers don’t need to use brute force because they can guess your password more quickly, without trying them all.
Another protection they give is to not allow access to your data to anyone but you. LastPass has failed to do this for a certain number of customers. It’s unknown whether any of the other providers have done the same—they might have kept the data safe, or … not yet been outed.
It’s known that some people’s password data has been expropriated. This shouldn’t matter because it’s just a pile of bits that is undecryptable without the password.
If you had a weak master password at the time that your data was known to have been stolen, then you’re at risk. You still have a chance to change all of your important passwords, though, before someone guesses your master password and gains access to the current passwords. If you’ve managed to change your passwords before they guess your old master password, then getting access to your old passwords gives them nothing.
Some providers (and security analysts) recommend keeping your ball of data locally, never uploading to the cloud. This is much less convenient and not something I’m personally willing to do. I would rather have a super-strong password that makes obtaining my encrypted data useless.
Layers of security:
- Algorithmic protection
- Strong password
- No access to data
Algorithmic protection is only as good the password. “No access to data” is a secondary layer. If it’s compromised (as was the case for some users at LastPass), then you’re left only with algorithmic protection + strong password. If you didn’t have a strong password, then you’re compromised, but you should have never been relying only on “security by obscurity” anyway (i.e., the fact that no-one had access to your data but you).
So, to sum up:
- I prefer a cloud-based password solution for the convenience, despite the risk that the ball of data could be stolen
- Your data can be stolen from any cloud-based provider (not just LastPass)
- Choose a strong master password to prevent brute-force attacks
- If you didn’t have a strong master password when your data was stolen, then:
- Change your master password NOW to avoid the same problem in the future
- Change as many of your passwords as you can to new ones
- Hope that no-one got there before you did
- If you had a strong password, then you don’t need to worry too much because your data is still safe. Only one of the layers has been penetrated.
- It hasn’t been able to forward to ProtonMail because of spam-ID restrictions since the beginning of 2023, so I have to reluctantly use an old gmail address for now.
- More and more sites are just rejecting Spamgourmet’s addresses as “not valid”. I’ve even noticed that some sites disallow my login because they’ve retroactively decided that my valid login—a SpamGourmet address—is no longer valid. I have to reset the password, but cannot because the site is also incapable of sending me an email to that address. This is all bad software and stupid policies. None of this is not SpamGourmet’s fault, but it’s making it harder and harder to use their addresses.
Comments
#1 − Finally deleted my LastPass account
I finally got around to deleting my LastPass account. I switched half a year ago to ProtonPass and never looked back.
“I have, after many years with LastPass, switched to ProtonPass. It’s included with my other Proton tools. The UI is more straightforward and friendlier (even if it’s not yet as good at detecting password changes and account-creation as LastPass). There is also the issue of LastPass having been infiltrated a few times. Thanks for the service over the years.”